AS THE U.S. SPACE FORCE CELEBRATES ITS 5TH ANNIVERSARY, SPACE SYSTEMS COMMAND STANDS READY TO PROTECT THE NATION’S SPACE ASSETS.

When the United States first began launching satellites more than half a century ago, the main threats to those valuable pieces of hardware were the natural phenomena of the space environment, such as excessive radiation and perhaps a collision with a meteorite.

“The trials and tribulations of how to build space craft was the hard part, not thinking that there could be some sort of destructive force trying to go after it besides the harsh environment,” Dr. Scott C. Theiring, Director withn Project West Wing of the Aerospace Corporation, said. “The average person doesn’t give (satellites) a whole lot of thought,” Theiring said. “They have the sense that GPS is based on satellites, but they’re not really thinking that there may be some sort of threat to GPS or other systems.”
Today, however, the threat to U.S. space assets is real and growing. Space debris from discarded and defunct space vehicles increases the threat of collision and adversaries have, and continue to develop, weapons to deny, degrade, and even destroy space assets, with effects ranging from temporary to catastrophic and permanent.
“The Space Force was established because these threats are real and significant,” said USSF Major Neal Carter, Deputy Director of Intelligence at SSC. “Our job is to go after those threats so that the U.S. and its allies can operate freely in space.”
Carter, a former Marine, vividly remembers using space assets as a warfighter on the ground — from GPS to satellite communications and space based ISR (Intelligence, Surveillance and Reconnaissance) — and even missile warning on one occasion.
“Desert Storm in 1991 is widely considered the first space war,” Carter said. “That’s when the U.S. military and coalition forces started using GPS-guided munitions, and we started to see that all these things that operate in space help us achieve lethal effects on the battlefield. Whether it’s GPS, satellite communication, or space-based ISR to operate from a military standpoint, we’ve essentially been using assets in space since the early ‘90s, and it’s only multiplied since then. The U.S. Navy cannot sail without SATCOM, GPS and ISR. Bombers can’t fly and hit their targets without literally everything the Space Force provides. Everything we do benefits the joint force in a meaningful way.”

The U.S. Space Force (USSF) and Space Systems Command (SSC) officials are only too aware of the threats posed and they are mission-focused on measures to protect and defend these space assets.
For example, the USSF is reevaluating its space architectures and moving toward using multiple satellites in proliferated constellations in Low Earth Orbit (LEO) instead of a few large, expensive satellites tha are resident in Middle Earth Orbit (MEO) or Geostationary Orbit (GEO), which require more rocket fuel to place them on-orbit.
If one satellite in a proliferated LEO (pLEO) constellation is damaged or destroyed, it is far easier and less expensive to replace that spacecraft, and the capabilities provided by that satellite constellation may not be compromised as multiple satellites in that constellation remain operational.
The satellites SSC launches into space today are entering orbit with advanced anti-jamming technology on board, and USSF’s space domain awareness capabilities are continually monitoring space for everything from missiles to rogue adversary satellites that possess the capacity to harm U.S. satellites.
When the United States first began launching satellites more than half a century ago, the main threats to those valuable pieces of hardware were the natural phenomena of the space environment, such as excessive radiation and perhaps a collision with a meteorite.
“The trials and tribulations of how to build space craft was the hard part, not thinking that there could be some sort of destructive force trying to go after it besides the harsh environment,” Dr. Scott C. Theiring, Director withn Project West Wing of the Aerospace Corporation, said. “The average person doesn’t give (satellites) a whole lot of thought,” Theiring said. “They have the sense that GPS is based on satellites, but they’re not really thinking that there may be some sort of threat to GPS or other systems.”

Today, however, the threat to U.S. space assets is real and growing. Space debris from discarded and defunct space vehicles increases the threat of collision and adversaries have, and continue to develop, weapons to deny, degrade, and even destroy space assets, with effects ranging from temporary to catastrophic and permanent.
“The Space Force was established because these threats are real and significant,” said USSF Major Neal Carter, Deputy Director of Intelligence at SSC. “Our job is to go after those threats so that the U.S. and its allies can operate freely in space.”
Carter, a former Marine, vividly remembers using space assets as a warfighter on the ground — from GPS to satellite communications and space-based ISR (Intelligence, Surveillance and Reconnaissance) — and even missile warning on one occasion.
“Desert Storm in 1991 is widely considered the first space war,” Carter said. “That’s when the U.S. military and coalition forces started using GPS-guided munitions, and we started to see that all these things that operate in space help us achieve lethal effects on the battlefield. Whether it’s GPS, satellite communication, or space-based ISR to operate from a military standpoint, we’ve essentially been using assets in space since the early ‘90s, and it’s only multiplied since then. The U.S. Navy cannot sail without SATCOM, GPS and ISR. Bombers can’t fly and hit their targets without literally everything the Space Force provides. Everything we do benefits the joint force in a meaningful way.”
The U.S. Space Force (USSF) and Space Systems Command (SSC) officials are only too aware of the threats posed and they are mission-focused on measures to protect and defend these space assets.
For example, the USSF is reevaluating its space architectures and moving toward using multiple satellites in proliferated constellations in Low Earth Orbit (LEO) instead of a few large, expensive satellites tha are resident in Middle Earth Orbit (MEO) or Geostationary Orbit (GEO), which require more rocket fuel to place them on-orbit.
If one satellite in a proliferated LEO (pLEO) constellation is damaged or destroyed, it is far easier and less expensive to replace that spacecraft, and the capabilities provided by that satellite constellation may not be compromised as multiple satellites in that constellation remain operational.
The satellites SSC launches into space today are entering orbit with advanced anti-jamming technology on board, and USSF’s space domain awareness capabilities are continually monitoring space for everything from missiles to rogue adversary satellites that possess the capacity to harm U.S. satellites.
These and similar efforts are driven by a laser focus on emerging threats. The most concerning of these are cyber attacks, electronic warfare, directed energy weapons, kinetic energy weapons, high altitude nuclear detonation, and on-orbit attacks.

Adversaries can blast their own signals at satellites, jamming them and preventing important space data from getting to the warfighter. Illustration by Russ Isler, SSC.
Cyber Attacks
A cyber attack can occur when an adversary gains access to a computer system and inserts malicious code. Attacks such as these can include hacking on-orbit satellites; infiltrating the ground-system computers that control and receive data from the satellites; compromising drones; or affecting other computer systems, which, in turn, can compromise everything from satellites to power grids and other crucial infrastructure.
Brian Sessler, chief of SSC’s S6 cyber security division, said for U.S. Department of Defense custom and “GOTS” space systems (Government- Off-The-Shelf), as opposed to COTS (Commercial- Off-The-Shelf), an adversary’s attack is less likely to be a direct attack on the satellite itself and more likely to be an initial point of entry attack on and through the ground command and control network.
“There is the potential for a direct signal to get code injection onto the satellite, but it’s going to be much more difficult on a GOTS system because of the rigor that is put into hardening the system,” Sessler said, adding that commercial systems can be less expensive. However, SSC has to vet the supply chain and may have to engage in additional hardening to make the systems more resilient to attack.
“One of the primary goals of a cyber attack is for reconnaissance,” Sessler said. “Whether that’s for cyber reconnaissance, to further map the system and networks with the goal of maximizing attack effects on the system or just to exfiltrate mission data for intelligence purposes.”
In terms of destruction, most cyberattacks are not causing the computer system to explode or erupt in flames, Sessler said. It’s more of a functional kill — impacting the availability of the system or the servers and denying warfighters access to the crucial services those systems provide, such as communications or indications and warning data from a satellite.
“Our space systems are force multipliers: there are second- and third-order effects if you take out one of our GPS satellites, for example,” Sessler said. “How many other weapons systems, rely on precision navigation and timing data and services from that satellite constellation? The same can be said for our communications and sensor satellites that are providing critical indications and warning data. Our adversaries are going to want to affect their availability, which is going to affect the kill chain and our ability to execute the mission.”
But it’s not just protecting systems once they’re operational, Sessler explained. Cyberattack threats apply across all phases of the acquisition process and need to be addressed early.
A lot of it comes down to making sure all personnel are trained and able to recognize phishing attempts, social engineering as well as insider threats that could compromise a system early in the design and development process.
While the areas of vulnerability for a satellite might be different than for a terrestrial system, Theiring said, much of the protective measures are similar: a layered defense, monitoring for unusual traffic, encryption, making sure only certain users are allowed to issue commands under particular conditions, and other measures.
Applying a DevSecOps process — development, security and operations, a modern approach to software development that integrates security throughout the development process — is essential, Sessler said, as well as constantly conducting penetration testing to make sure systems are hardened against attacks, and making sure individual components aren’t corrupted before being integrated with a larger system architecture.
What better way to make certain hackers can’t attack on-orbit satellites than to launch one and challenge hackers to attack it? Hack-A-Sat, the annual hacking competition sponsored by the U.S. Department of the Air Force, SSC, and the Air Force Research Laboratory (AFRL) invited teams from all over the world to hack an actual, on-orbit cubesat last year — with the goal of being able to use learnings from the competition to help make future satellites more secure.
“Cybersecurity is very tough because the adversary only needs a pin hole in the attack surface,” Sessler said. “We’re defending against the entire surface, all potential attack vectors, and the adversary only needs to find that one pin hole. Cybersecurity starts early in the life cycle, but at every step of the acquisition process, we need to stay vigilant.”
Electronic Warfare (EW)
Satellites can also be vulnerable to electronic warfare in the form of jamming and “spoofing” U.S. satellite signals.
“There are a many different ways an adversary can employ electronic warfare,” Carter said. “There is ground-based EW, airborne EW, maritime-based EW as well, but what we’re seeing more and more is space-based EW. There are also different types of electronic warfare – electronic attack, electronic support and electronic protection.”
Electronic attack is essentially radiating large amounts of electromagnetic energy onto a satellite receiver or a radio antenna, and that makes quite difficult — if not impossible — for (an operator) to receive the intended signal.
Carter provided the example and said, “I have two kids, and they can be very loud. If I’m in the kitchen, washing dishes, and my wife is in the living room and she’s trying to tell me something from across the room, but the kids are talking so loudly, it’s just impossible for me to hear her — that’s jamming.”
“You’re not necessarily doing anything to the intended receiver; you’re just making it impossible for that receiver to hear over the noise,” Carter said.
“EW has been around for more than 100 years, but as warfare evolves — from the land domain to the air domain to the sea domain — now adversaries can target space assets on-orbit. Satellites communicate with receivers on the ground and adversaires have found ways to, essentially, ‘scream’ so loudly that the ground receivers can’t hear the signal we’re trying to send.”
How does the USSF combat this method warfare? By hardening systems and determing procedures by which the receivers are able to signal-hop, Carter said. Another method is to just “scream louder” by boosting the power of the intended signal.
“If an adversary figures out we’re communicating on a certain frequency, then they’re going to start jamming that frequency,” Carter said. “So, instead of staying stationary on that frequency, we may configure our radios to frequency-hop, making it difficult for our adversaries to jam us.”
Spoofing is when someone takes a radar signature or other electronic indicator and projects it somewhere else, making the object appear to be in a different location, Carter said. For example, making a ship appear to be in a different location than it actually is, and making it harder for someone to target that object and close the kill chain, that’s spoofing.
Directed energy weapons from the ground are one of the ways an adversary could attack a satellite. Illustration by Russ Isler, SSC..pdf
Directed Energy Weapons
In a similar vein, directed energy weapons can be used to damage and degrade equipment and signals. Such an attack might take the form of a ground-based directed energy weapon, radiating lasers to blind or dazzle satellite sensors on-orbit — or it could be a directed energy weapon on-orbit, Carter said.
“Having a ground-based weapon gives the adversary a little more power boost, and they can maintain that system on the ground, but in orbit, you can get a lot closer to the target,” Carter said. “There are trade-offs for both of those, and we expect to see more examples of this in the coming years.
“If we have an ISR satellite that we’re using to observe airfields, ships, missiles, or ground troops – all things that the joint force and the national command authority need to build intelligence assessments – and there’s a directed energy weapon with a laser dazzler or other type of emitter that’s engaging and cooking that satellite, the sensors on that bird are fried,” Carter said. “If we can’t see our targets on the ground, then we can’t get that intel to the warfighter, the commander, or the president. It’s a significant threat if adversaries can go from satellite to satellite, pinpointing and targeting our ISR birds.”
Whether the damage is temporary or permanent depends on exposure time and proximity — and for an on-orbit weapon, how close the adversary can get before the rogue satellite is spotted, and countermeasures are activated, Carter said.
In addition to physically hardening satellites to protect them, another way to safeguard satellites involves making certain they are maneuverable and also ensuring the U.S. and allies have the ability to detect when a satellite is being attacked, Carter said.
“With material hardening comes other drawbacks and tradeoffs. If you put shielding on your system, you could weigh it down too much, and the more weight you put on a satellite, the more expensive it becomes to launch, maintain, and keep in orbit. There’s a lot of considerations we have to account for as we’re designing a satellite and before we launch it.”

Directed energy weapons from the ground are one of the ways an adversary could attack a satellite. Illustration by Russ Isler, SSC
Kinetic Energy Weapons
Kinetic energy weapons are weapons designed to destroy space assets, either by colliding with them or by using warheads to destroy them. Kinetic weapons pose an additional threat in that the fragments of the destroyed satellite then become space debris, thereby posing a threat to other space vehicles.
“The most visual representation that we can remember is the movie ‘Gravity’ (2013),” Carter said. In that film, Russians destroy one of their defunct satellites, and the resulting space debris field destroys a space shuttle, damages the ISS, and takes out several communications satellites.
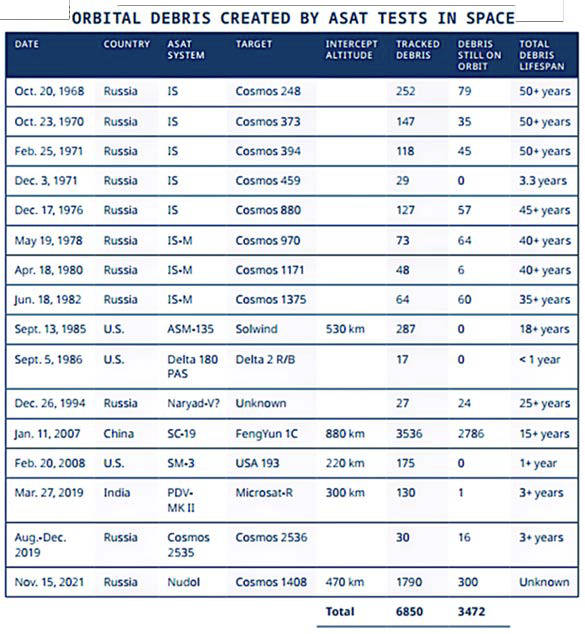
Both Russia and China have demonstrated the ability to use direct-ascent anti-satellite (ASAT) weapons. China tested an ASAT weapon in January of 2007, destroying a defunct Chinese weather satellite, and resulting in the creation of a debris field that possessed more than 3,000 pieces of space debris.
“A 2023 report from the National Space Intelligence Center was looking at how many pieces of debris were still in orbit from the 2007 destruction that China executed, and the estimate was there were still 2,700 pieces still in orbit, basically a decade and a half later,” Theiring said. “So those things are still flying around in space and adding to that environmental threat. And they’re not clearing out of that minutely thin atmosphere that high up.”
Objects in LEO could be travelling as fast as 17,000 mph, so depending on the size of the object and what it hits, space debris can be extremely destructive, Theiring said.
“If it’s the size of a grain of sand, the satellite lives to survive another day, but if it’s the size of a baseball, it’s probably going to be catastrophic,” Theiring said. “It depends on what it hits and then it becomes very random – if it hits the solar cells and causes the half-loss of power, maybe half the mission is still working. But if it hits a key component, the satellite is dead, even if it was just a small piece of debris.”
In November of 2021, Russia tested an ASAT and destroyed one of their older satellites, generating more than 1,500 pieces of trackable space debris in LEO and forcing two cosmonauts (who happened to aboard the International Space Station at the time) to shelter in emergency vehicles. Even today, the ISS is still occasionally having to maneuver to avoid debris from that 2007 Chinese ASAT test.
“Being able to set those norms — and not just from a human spaceflight perspective but a space defense and space warfare perspective — is important,” Carter said. “If nothing else, our job in the Space Force is to prevent conflict as much as it is to win in the event of a conflict. I joined Space Force so my kids don’t have to fight the wars I did.”
Space Domain Awareness (SDA) — not just knowing where U.S. space vehicles and those of our partners are located, but also those of our adversaries — tracking space debris, and characterizing threats and hazards — is all part of the USSF’s decision-making process in threat identification and determining what phenomenon poses a threat and what is benign, Carter said.
High-Altitude Nuclear Detonation
 An adversary could launch a nuclear weapon and detonate it at a high altitude, creating a radiation burst that could damage or destroy satellites. Illustration by Russ Isler, SSC.
An adversary could launch a nuclear weapon and detonate it at a high altitude, creating a radiation burst that could damage or destroy satellites. Illustration by Russ Isler, SSC.
An adversary could also launch a nuclear weapon and detonate it at a high-altitude, creating a radiation burst that could damage or destroy satellites.
Adversaries do have this capability, and it’s not new, Carter said. Both the U.S. and the former Soviet Union developed this capability decades ago, in the 1950s.
“The higher the nuclear detonation is in altitude, the bigger the problem because of yield,” Carter explained. “When you have a high altitude or high orbit, the yield that the altitude gives the radiation, and that energy, creates problems for other orbits, not to mention the Earth’s protective magnetic belts. It has the potential to wreak havoc on communication satellites and GPS satellites and everything we depend on for our way of life. It’s a huge threat.”
Employing this threat/putting this threat into action/ acting on this threat would make space inaccessible for not only the United States, but for the adversary as well and “we’d hope that’s a good deterrent against deploying that kind of weapon. But we can’t go off hope alone,” Carter said.
In addition to SDA and strong missile detection and tracking systems, “open lines of communication with our joint partners and international allies -- as well as our adversaries — is important,” Carter said. “Just because we may not be on the best terms with a nation state doesn’t mean we shouldn’t talk to them to prevent miscalculation and misunderstanding and ultimately, a tragedy.”
Orbital Attacks
Adversaries have also demonstrated the ability to launch satellites with smaller satellites nested within them as well as satellites with robotic arms. While such capabilities could be used for peaceful purposes — repairing or refueling satellites — this kind of technology also could be used to deploy satellites capable of disabling or destroying other spacecraft.
“That’s the tricky thing about space operations and space warfare in general,” Carter said. “A lot of what a nation state can launch into orbit can appear benign and peaceful, but that’s kind of the cover story.
Just because an adversary says ‘This is for peaceful purposes; this is for repair operations,” doesn’t mean it’s not worth us paying close attention. Does it have the capability of maneuvering near or onto our vehicles and doing some serious damage? That’s something we’re paying very close attention to.
“At least one Chinese satellite has been identified as having a robotic arm on it, and that satellite moved close to an old Chinese satellite and moved it into a super synchronous (graveyard) orbit,” Theiring said. “The use of robotic arms are required for refueling or for servicing and other peaceful and productive uses. However, the skillsets required for that also overlap with the ones required for more nefarious purposes. In this case, the towing of that satellite was a net benefit – it got rid of a piece of space junk in GEO.”
Hardening space vehicles, ensuring maneuverability and early detection of threats are all good defensive measures to mitigate the threat, Carter said. However, so, too, is a pLEO constellation where many smaller, less expensive satellites can provide more resilience.
In many respects, space is still a very new frontier. The Outer Space Treaty of 1967 established a framework for space law, but it is proving to be outdated as more nations participate in space and new technologies. Plus, greater numbers of satellites increase the need for coordination and universal rules.
The unique components of orbital mechanics also mean that if an adversary decides to destroy another country’s satellite, they could end up jeopardizing more than just one nation’s spacecraft. Additionally, there’s the sticky problem of attribution: how do countries determine who is responsible for damaging another nation’s space vehicle?
“Attribution is the tricky part about space warfare – such as the strategic implications of a rendezvous-and-proximity operation,” Carter said. “It’s easy for (airplane) pilots to see some sort of incursion: a Russian plane flying in American air space, near Alaska. They can see the markings, they know what type of planes the Russians fly, and the pilots can communicate with and take pictures of their Russian adversaries.
“It’s a lot harder to do that in orbit – and then convince the international community that it’s occurring. And with that, are we burning sources and methods of how we collect the intelligence.” Carter said.

“Even as recently as 10 years ago, space wasn’t as competitive, congested or contested to the point where we needed a dedicated military service to operate solely in the space domain,” Carter said. ‘Now, it couldn’t be more important, and our role will only continue to grow. As commercial interests start to expand into every orbit and cislunar space, our job is only going to get harder and become more important.”
Space Systems Command is the U.S. Space Force field command responsible for acquiring, developing, and delivering resilient capabilities to protect our nation’s strategic advantage in, from, and to space. SSC manages a $15.6 billion space acquisition budget for the Department of Defense and works in partnership with joint forces, industry, government agencies, academic and allied organizations to outpace emerging threats. Our actions today are making the world a better space for tomorrow
For additional information, contact Space Systems Command at SSC@spaceforce.mil and/or follow on LinkedIn.
Author Lisa Sodders writes the monthly Space Systems Command column for MilsatMagazine.


