Given the growing importance of assured military satellite communications (MILSATCOM) to successfully execute global missions, the Department of Defense (DoD) is facing significant near-term decisions concerning the future of satellite communications. It is extremely important to make the right decisions, objectively and intuitively, as MILSATCOM systems take decades to acquire and field. Communications that are not assured potentially jeopardize mission execution with catastrophic implications for our national security.

Characterizing assured communications becomes critical in the midst of dramatically changing budget and threat environments. Two terms that have been the subject of significant debate, resilience and protection, are key to this characterization. In the past, assured communications in an adversarial environment was summarized by the term protection (e.g., for the Milstar system) and called protected communications.
Today the term resilience has gained prominence due to the rising concern of physical attacks. Resilience in today’s context emphasizes a system’s ability to continue providing required capabilities in the face of damaging attacks. Protection, in this light, now refers to a system’s robustness and its ability to withstand threats without any degradation in capabilities. Separately, it is imperative that we understand the decisions ahead and make the right ones. To avoid confusion, we will use the term ‘assured communications’ to represent both resilience and protection.
A framework that objectively and intuitively defines and measures assured communications becomes imperative. This framework should identify the underlying architecture objectives that will provide the highest value in reducing risks from adversary threats. We believe the following characteristics must be clearly and simply established as the foundation for such a framework:
1) Definition: Enabling a common understanding and dialogue among community leadership
2) Measurement: An intuitive and objective approach that avoids subjective dialogue and conclusions
3) Principles: A simple, intuitive application to space architecture and acquisition
This article will provide such a detailed framework to objectively and intuitively assess assured communications capabilities of future MILSATCOM architectures being considered.
The Growing Importance Of Assured MILSATCOM
Mission success must always be the military’s top priority. Relevant, timely and actionable communications are crucial for ensuring successful military campaigns. The denial of such capability can be disastrous. With continuing affordability and capability challenges, the DoD has turned to technology as a force multiplier.
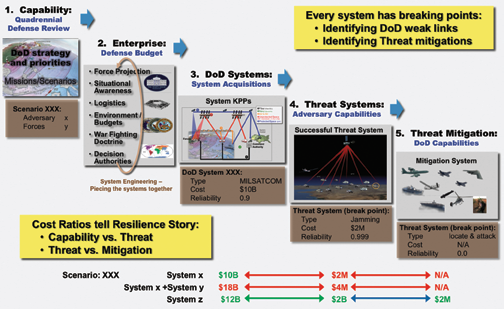
Figure 1. Breaking down the problem to assess assurance.
As military systems and weapons increase in capability and complexity, MILSATCOM needs to keep pace with improvements in capacity, connectivity and protection from threats. This growing dependence and demand on communications places a heavy burden on the need for future assured MILSATCOM architectures. Adversaries can neutralize DoD systems and broader infrastructures costing billions, if not trillions, of dollars with tactics that cost significantly less, putting our national security in peril.
Currently, most of the global, mobile DoD enterprise is supported by unprotected MILSATCOM vulnerable to readily available, low-cost threats. One of the most important investment decisions our leaders face today is which communications foundation they will build upon, fully realizing the far-reaching effects on future military power as asymmetric threats to MILSATCOM are emerging precipitously.
The Dramatically Changing Threat Environment For MILSATCOM
In the past, MILSATCOM threat assessments were primarily focused on the most unique, complex weapon that an adversary could develop. The proliferation of low-cost, readily available technologies is causing dramatic upheavals in electronic, cyber and physical threat landscapes, and forcing fundamental changes in the way we look at assured MILSATCOM.
Today, adversaries have access to a wide range of readily available commercial technologies that threaten all aspects of MILSATCOM systems—from gateways, to satellite ground control, to terminals and in to space. Off-the-shelf technologies are becoming increasingly capable of degrading, disrupting and denying access to space. With a multitude of low-barrier-to-entry threats, these technologies significantly increase an adversary’s asymmetric advantage and the likelihood of a low-cost weapon disabling an expensive space system. Such technologies can be fielded with very short cycle times and with little attribution. They give an adversary the ability to experiment, test, train, distribute, mobilize and reconstitute assets quickly, making threats highly reliable and very difficult to find and mitigate.
An example of where low-cost threats can be found is in the exploding worldwide global mobile communications market. Capacity and access are expanding to the far reaches of the globe. User terminals are exponentially growing in number, shrinking in cost and becoming a normal part of society. Inexpensive, ubiquitous SatCom terminals are potential jammers and disruptive barriers for achieving assured MILSATCOM in a frequency spectrum widely shared with consumers, commercial companies and adversaries. The impact of electronic threats (e.g., jamming) seriously threatens mission success.
This changing threat environment is no less true for commodity products that enable cyber and physical attacks on MILSATCOM assets. The April 2013 coordinated sniper attack on a California power substation reported in the Wall Street Journal provides ample evidence that physical, asymmetric attacks are a real, viable threat to space system ground elements. In a physical attack that took the perpetrators only 19 minutes to disable 17 giant transformers, it took nearly a month for utility workers to restore power. Many of the space systems the U.S. government employs in its MILSATCOM network share the same weakness this power substation exhibited—an inability to fend off a coordinated, asymmetric physical attack on ground assets.
The Context Of Assured MILSATCOM
Defining and measuring assured MILSATCOM means understanding where and how it fits within the DoD context. The Quadrennial Defense Review sets a long-term course for assessing threats and challenges and for rebalancing strategies, capabilities and forces to address them. Rebalancing the DoD is an expansive task that looks across the services’ (Army, Navy, Air Force, Marines), force projections, logistics and situational awareness capabilities, as well as the environment and doctrines that guide the concept of operations and decision-making to execute missions/scenarios critical for our national security. Being able to execute established prioritized missions requires coordinated, enterprise-wide efforts (see Figure 1). The enterprise must determine how different systems interact to execute missions with the best performance and investment solutions.
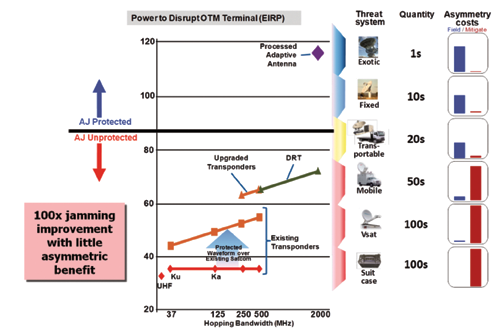
Figure 2. Jamming threats in MILSATCOM systems.
Enterprise assurance is tied to overall systems assurance. A threat to mission execution is, in reality, a threat to one or more enterprise systems. Each system acquired within the enterprise satisfies key performance parameters (KPPs) critical to effectively executing military capability. KPPs normally define the minimum acceptable performance threshold a system must deliver. In this light, system assurance is a measure of its ability to support the KPPs in the face of adversarial actions. For threats to be successful, it needs to ‘break’ a DoD system and compromise its ability to meet KPPs.
This is when breakpoints and corresponding solutions for mitigating threats become keys to understanding levels of assured MILSATCOM a system provides. An adversary will seek out “weak links” or vulnerabilities that can be exploited easily and inexpensively with maximum impact, and often with little perpetrator attribution—a definite asymmetric advantage for an enemy. Conversely, an assured MILSATCOM system will drive the asymmetry in the other direction—where an adversary must expend substantial cost and effort, and face potentially large political consequences to achieve any amount of impact.
The challenge for MILSATCOM system designers is avoiding a myopic view focusing on a particular type of threat while leaving other vulnerabilities unaddressed. Additionally, as we seek solutions to counter sophisticated threats [e.g., anti-satellite weapons (ASATs)], we must be careful to not inadvertently overlook opportunities for much simpler, less sophisticated threats. Unless a MILSATCOM system design addresses all forms of threats with a balanced approach, any investment in “partial assured MILSATCOM” is of questionable value. Consequently, an evaluation of assured MILSATCOM should focus on identifying the weakest links and potential asymmetric threats.
Definition Of MILSATCOM Assurance
Following the framework’s guiding characteristics, we propose to define and measure assured MILSATCOM systems based on the economics of the situation, namely the threat system costs and corresponding mitigation costs. This provides a simple, well-understood tool to quantitatively assess, compare and contrast the assured communications merits of various MILSATCOM systems. Cost provides a fundamental metric to characterize system breakpoints: It is deterministic, provides an objective basis for military decisions, provides a strong intuitive foundation, and establishes a sound basis for assessing subjective criteria (geo-political, deterrence, attribution, escalation, etc.).
Assured MILSATCOM can be characterized by system breakpoints where a specific threat system compromises (breaks) mission success and mitigation solutions to such threats. An economic definition and measurement must bring light to the likelihood and consequence of a threat compromising the system. The primary economic data points in assessing assured communication are DoD enterprise and system costs, threat system costs and corresponding threat mitigation costs. Enterprise and system costs presumably will be very high and threat costs will be significantly less. In this light, characterizing assured communications revolves around threat system costs and the resulting mitigation costs.
We define assured MILSATCOM as those systems that require adversaries to adopt high-cost threats to succeed, and ones that have much lower costs for mitigating the threat. Systems vulnerable to low-cost threats, or threats with no mitigation options, do not characterize assured communications. Forcing an adversary to use very expensive tactics is critical to assured MILSATCOM. This characteristic drives many relationships affecting affordability, difficulty, complexity, attribution and likelihood and can be summarized below:
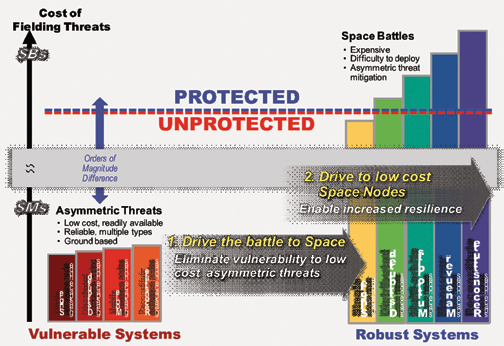
Figure 3. Summary of Assured Communications findings.
Assured MILSATCOM System = Threat System Costs >> Threat Mitigation Costs
An example of this relationship can be portrayed from physical threats (e.g., small arms, guided munitions, etc.) against systems dependent on ground nodes (e.g., hubs, gateways, teleports, and control stations). The cost of threat systems for such cases can be as low as $100s without any affordable threat mitigation options. Duplications of such nodes do little to deter (e.g., attribution, difficulty, complexity, affordability or likelihood) the significant economic advantage from such a threat.
Alternatively, autonomous processed systems which avoid the vulnerability of ground nodes require the battle be waged in space force a whole different magnitude of threat system cost and numerous asymmetric mitigation options. To assess the value of different assured systems, we can compare the cost of systems with similar economics. These value assessments are directly linked to mission success, and therefore to mission value, giving decision-makers more clarity. They also yield critical insight into the exact set of elements that will create an affordable and assured MILSATCOM architecture capable of achieving national security objectives.
Measurement Of MILSATCOM Assurance
MILSATCOM systems, threat systems and threat mitigation options can be characterized using classic, established system assessment disciplines and metrics. These disciplines provide established, intuitive and verifiable characterizations by type, cost and reliability. From these characterizations, any asymmetric advantage for or over the adversary can be clearly and intuitively identified. An abundance of tools (e.g., costing and reliability) make it easy to perform these assessments. The results don’t need to be highly precise—we’re looking mainly for large differences (asymmetric advantages) in cost. This lends itself nicely towards achieving objective, intuitive and common understandings on weaknesses and strengths that can easily be translated into specifications for MILSATCOM systems and architectures.
Example: Using Threat and Mitigation Cost To Assess Jamming Threats
Ground-based jammers are a good way to evaluate assured MILSATCOM communications using threat and mitigation costs. Figure 2, depicts an analysis of different types of jammers used to characterize breakpoints in transponded and processed MILSATCOM systems. The cost to field each threat system was compared to the cost to mitigate the threat. In MILSATCOM systems without anti-jam capabilities (e.g., transponded systems), a large asymmetric threat cost advantage exists that allows low-cost, mobile, blinking threats with large standoff distances to easily disrupt and deny mission success.
In MILSATCOM systems with anti-jam capabilities (e.g., processed systems such as AHEF) the asymmetric threat cost advantages are reversed and adversaries need to develop very expensive, easily attributable jammers to have any noticeable effects.
In general, the results in Figure 2 show that transponded MILSATCOM solutions provide adversaries a very high asymmetric threat advantage. To turn the advantage against the adversary, MILSATCOM systems with on-board processing forces adversaries to utilize large antennas that require fixed infrastructure to orchestrate effective jamming attacks. Large, fixed-jammer implementations with little effective standoff distances are easily attributable and become a significant asymmetric threat disadvantage for the adversary. This shows that sound system investment decisions can be made by using threat system costs and corresponding threat mitigation cost relationships as a relative measure of the value of assured communications.
Principles Of MILSATCOM Assurance
Two simple, yet effective, architecture principles can be gleaned from this framework to significantly improve assured communications in MILSATCOM systems (see Figure 3). The First Principle is about minimizing system vulnerabilities to low-cost, ground-based threats to eliminate an adversary’s asymmetric threat advantage. Asymmetric threat advantages allow adversaries to pursue threat escalation strategies using multiple, low-cost mobile tactics that are nearly impossible to find and eliminate in a timely manner. The equipment to carry out these threats can easily be bought in large quantities, enabling effective training and experimentation to determine best practices and designs.
This paves the way for strategies that employ significant reinforcements available to deal with mitigation issues through rapid reconstitution and recovery. These threats are available to many adversaries and can be used in coordinated attacks across multiple system nodes (e.g., primary and redundant uplink stations). This asymmetric threat advantage over MILSATCOM and space systems in general is what predominately enables the possibility of a “day without space.” By eliminating these low-cost threat asymmetries, adversaries are forced to choose more costly, more attributable threats and escalation strategies and a “day without space” becomes a much more remote possibility.
The Second Principle comes by eliminating low-cost, ground-based asymmetric threat environments and driving the battle to space. That makes threat systems very expensive and more attributable, effectively turning the tables in favor of the MILSATCOM system. This forces an adversary to follow a high-cost threat escalation path before achieves any significant success. These space-based threats are substantially more difficult and time-intensive to develop and deploy.
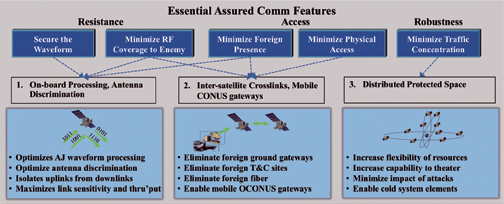
Figure 4. Achieving Threat Mitigation Objectives in an Architecture Implementation.
Very few adversaries have the sophisticated capabilities or wealth to pursue this path. Increasing assured communications in space can be further enhanced as we move to an architecture with low-cost space nodes. This enables MILSATCOM systems to affordably pursue architectures that are distributed with multiple orbits, making asset reconstitution possible. These nodes must still provide meaningful capability such that the system is affordable, manageable and meets the required KPPs.
For MILSATCOM assured communications to be strengthened, both principles must be intuitively understood and applied. These principles mandate a rethinking of the broader space architecture and the duplication of systems to achieve affordable, resilient capabilities.
Architecture Feature + Characteristics Of MILSATCOM Assurance
MILSATCOM acquisition teams, armed with a keen understanding of the key architecture features necessary to implement these principles, can more effectively determine where protection investments should be made. A preliminary evaluation identified the key features that drive the overall protection from electronic, physical and cyber attacks. Initial findings showed significant differences in the assured communications levels offered by different architecture types.
We identified the key elements driving these differences in Figure 4 by relating evaluation levels to underlying architecture features. Specifically, five threat mitigation objectives were identified that diminish or thwart known threats and vulnerabilities in MILSATCOM architectures, thereby minimizing opportunities for attack. The five mitigation objectives are:
(1) Secure the waveform
(2) Minimize RF access to the enemy
(3) Minimize foreign presence
(4) Minimize physical access
(5) Minimize traffic concentration
The first two objectives provide resistance against electronic attacks. The third and fourth objectives address accessibility to system elements that can be exploited in physical, cyber and electronic attacks. Finally, the fifth objective constrains the scope of an attack and ensures the system’s robustness against node failures. The level of assured communications against identified threats correlates directly to how well the architecture implements all five mitigation objectives. All features need to be implemented to prevent a weak link in the system architecture.
Most notably, the threat assessment revealed a strong correlation between the level of assured communications and an adversary’s access to MILSATCOM system elements. Systems with significant terrestrial access points, particularly at foreign locations, exhibited the greatest amount of exposure to various threats. Such access points—satellite control facilities, gateways, hubs and fiber networks—create numerous attack paths that are more easily accessed with significant consequences. They additionally provide an entry point to find further ways to exploit the system.
Achieving threat mitigation objectives effectively and affordably requires a carefully conceived architecture implementation. Attempting to “add protection” to a particular system element without considering the total system may give an illusion of protection, but leaves critical vulnerabilities and weak links open for exploitation. In contrast, an architecture implementation that addresses the five core threat-mitigating objectives in a balanced, holistic approach yields a highly resilient SATCOM system void of weak link vulnerabilities.

One such MILSATCOM implementation that realizes these mitigation objectives has these features (Figure 4):
(1) On-board processing with antenna coverage discrimination
(2) Inter-satellite crosslinks and mobile continental U.S. gateways
(3) Distributed space assets
On-board processing enables the most effective waveform, anti-jam processing and the highest link sensitivity. Additionally, it enables high-performing antenna beamforming algorithms that adapt coverage to minimize the impact of jammers. This results in a highly-secure waveform and minimal RF access to adversaries. By eliminating the need for ground-based hubs, on-board processing also greatly reduces an adversary’s physical access to system assets. Combining on-board processing with crosslinks allows global routing without dependence on vulnerable terrestrial fiber and eliminates the need for foreign gateways. Finally, distributed space assets reduce the concentration of traffic in any one node and minimize the impact of a node failure.
Summary
Faced with a highly-constrained defense budget and a world where adversaries have increasing access to more capable and sophisticated threats that can be used against U.S. space systems, it is critical that government and industry identify cost-effective investments for successfully executing key national security missions.
Northrop Grumman Aerospace Systems has developed an assured communications context and framework for MILSATCOM to help forge a common understanding and to ensure investments deliver the required value for system architectures, designs and acquisition. The framework provides definitions, measurement tools and guiding principles that allow an objective and intuitive assessment of assured communications capabilities of future MILSATCOM architectures being considered.
For further details regarding Northrop Grumman Space Systems division, please access http://www.northropgrumman.com/Capabilities/space/Pages/default.aspx

About the author
Greg Edlund is Director, Communication Systems Chief Engineer and Architecture for the Space Systems business area of Northrop Grumman Aerospace Systems. He’s responsible for integrating customer, user, mission and political issues with company products and technologies into high-value communication system solutions. Additionally, he leverages the sector’s space and airborne knowledge, solutions and technologies to provide integrated air / space communication architecture solutions.
Prior to Northrop Grumman, Edlund worked as an independent consultant primarily for Lockheed Martin and the U.S. government developing corporate telecommunications strategies. He played key roles for Lockheed Martin in capturing both the MUOS and Advanced EHF programs. Edlund joined The Aerospace Corporation in 1983, where he spent 13 years supporting Department of Defense, civil and national space programs.


