Currently, setting up a network in a brigade command post takes hours and requires 17 boxes of 1,000 feet CAT 5 cable, which weigh a total of 255 pounds, and specialized raised flooring.
Like the cabling, the flooring adds weight, footprint and set up time to the command post and takes up vital air cargo and truck cargo space. Why is this a problem? For starters, units often need to change base locations during combat operations to outmaneuver the enemy or avoid attack, requiring the entire command post to be moved, or jumped. The command post has to be set up in phases, with tent infrastructure, generators, network servers and satellite shots established first, after which soldiers run the cable to provide the local area network (LAN) to support the command post. This leads to long delays in availability of critical information services—and vulnerability during that time.
As the Army is rapidly developing numerous, new, network-based battle systems to take advantage of innovative technologies and applications, the complexity of command posts and information services provided to the warfighter continues to increase. These new technologies provide our soldiers with more situational awareness and information capabilities, but they come with a cost—a requirement to forward deploy those services. These added compute and networking resources lead to an even slower deployment.
Wireless To The Rescue
The US Army is now developing and testing a variety of wireless technologies including WiFi and LTE to eliminate the delays in setting up command post networks. By going wireless, command posts can eliminate cabling and reduce network set up and tear down times from hours to minutes, making jumps faster and safer.
Lt. Col. Joel Babbitt, product manager for WIN-T Increment 1, which manages the command post wireless capability, recently noted the value of wireless to operations: "Now, directly after the tents go up, units can turn on the WiFi 'hotspot' and bam—they have a LAN. Instead of the network coming up last, now the network comes up first. Wireless reduces a unit's most vulnerable time period. Plus, by eliminating LAN wiring, the need for specialized flooring is eliminated, reducing setup time further.”
Wireless Is Not New, Is It?
While IT professionals and civilians are highly experienced with the benefits of WiFi and LTE for business and personal use, WiFi and LTE have not been widely available to the warfighter due to information and cybersecurity issues and expense.
However, benefits are becoming available to soldiers for mission use cases, thanks to the recently launched National Security Agency (NSA) “Commercial Solutions for Classified” (CSfC) program.
CSfC enables organizations to transmit classified information using commercial-grade encryption solutions, eliminating the need for expensive, difficult-to-use classified equipment. The enabling technology for this program is an architecture that consists of two layers of Suite-B cryptography, therefore these systems are often referred to as Suite B solutions.
Specifically, this program allows commercial smartphones, tablets and laptops to be used to access classified information over WiFi and LTE.
In addition to these breakthrough capabilities, the CSfC program enables access to classified information using inexpensive, commercial technologies, providing additional benefits such as:
• Significantly reduced equipment costs
• Simplified equipment handling/security procedures
• Simplified key management
• Simplified personnel training
• Enablement of US coalition partners to access classified information without taking possession of controlled cryptographic items (CCI)
Previously, the only means to transmit classified information was via expensive, controlled, military grade encryption devices that required extensive handling procedures that proved awkward for mobility applications.
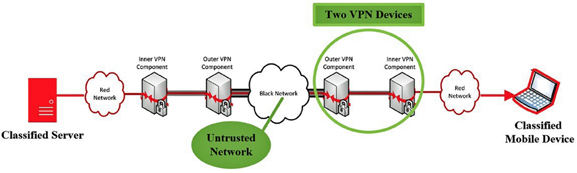
The simplified diagram on the following page shows a conceptual architecture of a laptop connecting to a classified server, over an untrusted (wireless) network, with two CSfC-approved VPN encryption solutions on either side of the untrusted network. Of note, the two VPN devices circled in green can be software running on the mobile device—enabling a software-only solution on the mobile device.
What, Exactly, Is CSfC?
CSfC is a program that enables the US Army and other Department of Defense (DoD) and government organizations to design and propose network solutions for classified information access using commercial technologies. The CSfC program consists of a set of core technical requirements, configuration requirements, test requirements, administration requirements and processes as shown in the overview below.
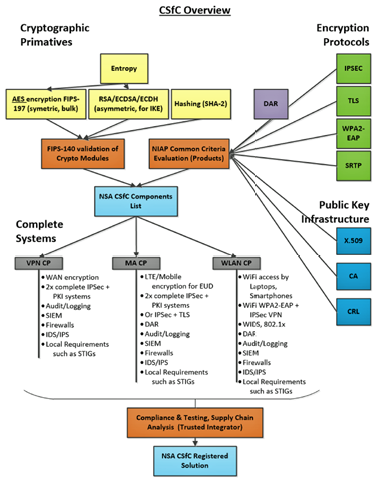
The CSfC overview at right includes the following main CSfC-related components.
• Shown in yellow, the “Cryptographic Primitives” are the approved algorithms and mathematics the NSA will allow for transmission of classified information
• Shown in green, the “Encryption Protocols” are approved to conduct communications between devices that transmit encrypted data. Most used today are VPN solutions providing data-in-transit encryption
• Shown in purple is “DAR” (Data-at-Rest) encryption technology. This type of technology is used to encrypt data stored on media such as hard drives, flash drives, etc.
• Shown in blue is “Public Key Infrastructure”, the approved technologies and protocols required to manage trust, encryption key generation and sharing
• Shown in brown are key validation and testing processes required by the CSfC program in order to comply with CSfC rules
• Shown in small gray boxes are the main NSA CSfC “Capability Packages” (CPs) specifying the required architecture, component and technical requirements, testing and personnel roles that must be followed and documented
• Shown in light blue are the two major “approval” statuses of technologies. The first is a listing of approved commercial (OEM) components that may be included in solutions. The second and final light blue box shows a completed solution, approved by the CSfC program and ready for deployment
While the CSfC program has the potential to transform communications for the soldier by enabling wireless, there is one significant issue: complexity. The CSfC program requires solutions to include comprehensive suites of security technologies at the command post or datacenter, and the CSfC program mandates the technologies are provided from different vendors. This creates a system configuration, management and training burden most organizations are under-equipped to solve.
Software Solution
A solution the US Army Wireless Command Post program is using to address the added complexity and training burden imposed by the two layers of encryption and extensive security requirements is PacStar’s IQ-Core Software. Using the firm's newly released CSfC Plug-in, IQ-Core Software simplifies the setup, configuration, and management of the underlying equipment and devices used in CSfC solutions. The software provides a base level of capabilities including:
• Enable the deployment of CSfC solutions, with attendant benefits, while reducing the amount of added complexity and training
• Provide a unified interface (“a single pane of glass”) to underlying equipment from multiple vendors
• Provide means to monitor multiple sets of equipment, in fixed/branch offices and tactical settings, enabling lightly trained operators to manage the equipment
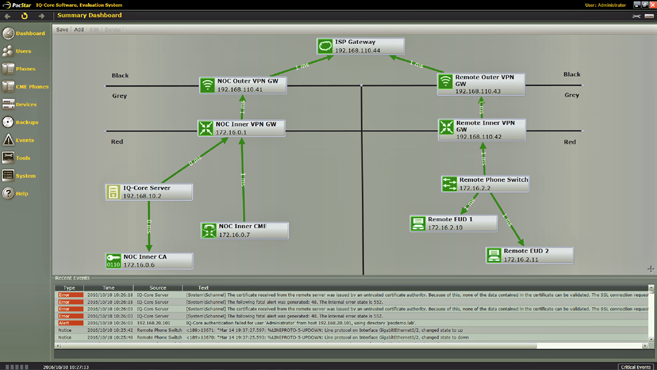
The IQ-Core Software CSfC Plug-in adds functionality specifically designed to make CSfC manageable.
VPN Setup Wizards
IQ-Core Software VPN setup and certificate generation wizards reduce the complexity of providing the correct information to the CSfC devices by providing step-by-step wizards, insulating lightly trained users from dealing with the command line interfaces and multiple UIs across the underlying devices.
VPN Monitoring/Troubleshooting
IQ-Core Software VPN monitoring capabilities include the ability to display, in real time, the connection and configuration status of one or more VPN devices. Within the status is an indicator of the active authentication and bulk encryption settings in use ensuring the connection is compliant with CSfC rules.
Certificate Management
The IQ-Core Software CSfC Plug-in automates the process of managing device certificates, a process that is error prone and requires extensive training. Reducing the opportunity for errors in this process helps ensure communications uptime and allows security administrators to focus on more important tasks. IQ-Core Software capabilities related to CSfC certificates include:
—Generation of certificate signing requests
—Display of certificate details and expiration dates, including expiration alerts
—Encrypted transmission of certificate signing requests
—Management of the signing process at either the deployed systems or at the NOC
—Management/monitoring of certificate authorities
—Providing certificate revocation checking via built-in OCSP and CDP functions
By using management solutions such as the software platform described above, the US Army is deploying CSfC solutions and gaining the benefits of WiFi and LTE in tactical settings, reducing command post setup time and enabling new classes of wireless applications, while limiting management complexity and training burdens.
pacstar.com
Charlie Kawasaki joined PacStar in early 2005 to lead the company’s technology strategy and future product roadmap for its proprietary product lines. He continues in that role today. Charlie has extensive experience in product development, software engineering, technology licensing, patent development, business development, product marketing, general management and M&A.

Prior to joining PacStar, Charlie provided his expertise to early stage technology companies, where he created dozens of software solutions in such industries as Internet infrastructure, cybersecurity, energy management, software utilities and relational databases. Charlie served as CEO of RuleSpace, Inc., which created world-leading technology for Internet parental controls applications used by companies such as AOL, Yahoo, SBC, BellSouth, and Microsoft. Before RuleSpace, he held product development and engineering management roles at The Palace, Inc., Creative Multimedia Corp., Central Point Software, Inc., Asymetrix Corp. and Microrim, Inc.
Apart from his various company roles, Charlie has a career long commitment to economic and industry development through association board service, including Software Association of Oregon, Regional Alliance for Infrastructure and Network Security, and Smart Grid Northwest, where he currently serves as development chair.


