Aitech Editorial Team
Today’s realm of modern warfare has been transformed by technological advancements reshaping traditional strategies. Emerging at the forefront of this shift are autonomous swarm operations.

The use of drones in military operations has been increasing from small scale operations to large, complex initiatives that are redefining the future of warfare.
Integrating advanced technologies like swarm operations within the CJADC2 framework can lead to more intelligent implementations for military combat forces.
The emerging
CJADC2 initiative
To provide our military warfighters with the improved ability to detect and act on information across the battle space, the Department of Defense (DoD) has implemented the Combined Joint All-Domain Command and Control (CJADC2) initiative.
The CJADC2 vision establishes a tactical, secure, and unified command and control network in a cloud-based environment that enables rapid receipt and transmission of intelligence, surveillance, and reconnaissance (ISR) data to interconnected networks across all branches of defense.
Military forces leveraging swarm capabilities can achieve superior situational awareness and rapid response times allowing for faster decisions to counter threats in contested rugged environments.
Understanding the complexity of integrating advanced technologies and tactics, techniques and procedures in swarm operations within the CJADC2 framework can ensure future mission success.
A unified communications infrastructure, known as the Digital Backbone, is playing a pivotal role in establishing the needed interconnected network of knowledge and data along the CJADC2.
5 Technologies Enabling Swarm Operations within CJADC2
The success of swarm operations relies on effectively harnessing specific technologies supported by the Digital Backbone, including:
• Artificial Intelligence (AI)
• Time-sensitive Networking (TSN)
• Autonomous Systems
• Sensor Fusion
• Cybersecurity
Artificial
Intelligence
Artificial Technologies (AI) technologies are critical enablers of swarm management within the CJADC2 structure. Through AI algorithms and machine learning (ML) techniques, military forces can enhance their ability to detect, analyze, and respond to swarm threats in real-time.
With the ability to analyze vast amounts of sensor data to detect patterns, anomalies, and potential threats, AI-driven swarm management systems can autonomously coordinate the actions of multiple agencies, optimizing their actions for maximum efficiency and effectiveness.
AI-driven decision and rapid response support systems enable proactive decision-making strategies to provide actionable intelligence to military agents and orchestrate successful swarm operations, while minimizing risk in harsh environments.
Time-Sensitive
Networking
Time-sensitive networking (TSN) enables real-time coordination essential for effective swarm operations within the CJADC2 foundation. TSN protocols prioritize data transmission to ensure low-latency communication for rapid decision-making and provides scalability so military forces can adapt their communication networks to the evolving demands of swarm technologies.
The flexibility of TSN enabled digital connectivity to armed forces as well as efficiently allocating bandwidth and resources to prioritize critical date transmissions, ensuring that essential information reaches decision-makers in real time.
While military operations become increasingly interconnected and data-intensive, using TSN protocols becomes vital for maintaining operation speed and achieving mission success in swarm environments.
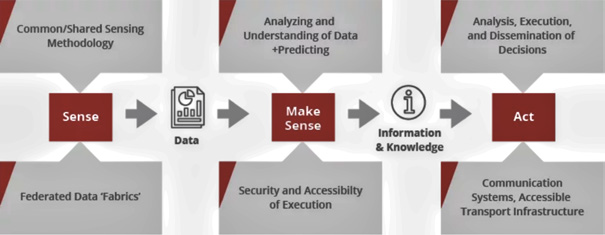 CJADC2 Action Chain and Process
CJADC2 Action Chain and Process
In order to overcome challenges of communication bottlenecks and delays, military forces can leverage TSN to enable agile and coordinated responses to dynamic swarm threats.
Autonomous
Systems
By enhancing surveillance capabilities through consistent monitoring of areas at a high-risk to swarm activity and early detection of threats, autonomous systems have become a growing and transformative capability within the CJADC2 framework to manage the transition of swarm capabilities into military technologies.
AI-driven autonomous systems enable uncrewed systems to assess the intent and behavior of swarms, adjusting their tactics, and maneuvers to maintain a tactical advantage. They provide rapid deployment and maneuverability, allowing for swift responses to emerging enemy swarm scenarios.
Autonomous systems allow a wider operational footprint by augmenting the capabilities of human-rated platforms, extending reach, and enhancing the effectiveness of military operations across all domains. Through autonomous capabilities and robotics, there is an unparallel scalability to analyze vast amounts of sensor data in real-time, enabling efficient adaptive responses to dynamic battlefield conditions.
Sensor
Fusion
Swarm operations under the CJADC2 framework use sensor fusion to enable the aggregation and correlation of information from disparate sources, ranging from traditional radar to advanced cyber sensors.
Combining inputs from all domains, land, air, sea, space, and cyber, sensor fusions compensate for individual limitations by providing an overall comprehensive understanding of the operational environment, enabling precise detection, and tracking of swarms in real-time scenarios.
To ensure the smooth distribution of information between crewed and uncrewed assets, command centers, and allied forces, data formats and communication protocols seamlessly facilitate communication and collaboration between systems and platforms to foster interoperability and synergy across diverse rugged domains.
Rugged electronics that offer high performance capabilities, such as the U-C850x Series, combines three pillars of modern data processing acceleration: CPU, iGPU and FPGA.
The series can meet the demand of real-time data processing for rapid decision making across command and control networks.
Sensor data combined with the intelligence within the CJADC2 framework provides military commanders with a more comprehensive understanding of the battlefield to anticipate swarm movements, identify vulnerabilities, and formulate effective response strategies.
By using sensor fusion, military forces can prioritize strategic actions based on the threat of swarms and deploy resources where they are needed most, ultimately maximizing operational impact and minimizing risk.
Cybersecurity
Given the reliance on interconnected digital networks and communication systems, cybersecurity measures are imperative to the CJADC2 framework when managing swarm operations.
The digital connectivity of these interconnected systems exposes them to various cyber threats, ranging from infiltration and data breaches to disruption and sabotage, meaning cybersecurity measures are paramount in safeguarding military operations from adversaries intent on compromising swarm missions.
Hardware-based cybersecurity frameworks, such as Aitechs AiSecure, prevents data breaches and firmware in products while allowing secure transmission and storage of sensitive data.
Comprehensive and proactive cybersecurity policies are crucial to establish and govern secure swarm-related technologies within military operations.

To ensure stringent security measures, military branches must practice continuous threat intelligence gathering, vulnerability assessments, and penetration testing to identify and address weaknesses in network defenses to preventatively identify and mitigate potential cyber-attacks on swarm operations before they can compromise mission integrity.
Cybersecurity training and awareness programs give military personnel at all levels the knowledge and skills to effectively identify and respond to cyber swarm threats.
Optimizing CJADC2 Technologies for Swarm Operations Collaborative efforts between military branches, allied forces, and industry partners in developing and implementing integrated technology solutions such as AI, TSN, autonomous systems, sensor fusion, and cybersecurity for swarm operations embody the spirit of joint experimentation and prototyping emphasized in the CJADC2 framework.
Harnessing these specific technologies using the Digital Backbone infrastructure to manage the rise of swarm operations enhances situational awareness, decision-making, and response coordination, echoing the objectives outlined in CJADC2 directives.
aitechsystems.com


