As technological advances allow GPS/GNSS1 devices to become more and more reliable, our lives are becoming increasingly dependent on accurate positioning and timing. Today, GNSS time is used to synchronize telecom and energy grids, while precise positioning is used to navigate drones and self-driving cars, as well as to automate agricultural and construction machinery.

As new use cases pop-up on a regular basis, our reliance on GNSS grows across the globe. This means that having secure, spoof-proof, communication channels between satellite and receiver becomes increasingly important to ensure Assured PNT (Positioning, Navigation and Timing,) especially in critical applications.

To further improve transmission reliability, the European GNSS system, Galileo, has developed the OSNMA (Open Service Navigation Message Authentication) anti- spoofing service. This service allows secure, end-to-end transmission from Galileo satellites to OSNMA-enabled GNSS receivers.
OSNMA will soon be available at no cost to users and has recently moved into the final testing phase. As ESA’s long- term partner, Septentrio has been contributing to the design and testing of the Galileo system since its inception 20 years ago. Today Septentrio is playing a key role in the OSNMA testing efforts, with the company’s receivers being the first to authenticate live OSNMA test signals.
Securing GNSS receivers against jamming and spoofing
OSNMA is one component of a vast array of technologies that protect GNSS receivers from interference.
Both jamming and spoofing are a type of radio interference that occurs when weak GNSS signals are overpowered by stronger radio signals on the same frequency. Jamming is a genre of “white noise” interference, causing accuracy degradation or even loss of positioning.
Spoofing is a more sophisticated form of interference that fools a receiver into calculating an incorrect location. During a spoofing attack, a nearby radio transmitter sends fake GNSS signals to the target receiver. For example, an inexpensive SDR (Software Defined Radio) can fool a smartphone into showing the user’s current location on top of Mount Everest.
You might have caught some spoofing events presented in the recent news. For example, C4ADS, an NGO conducting data-driven analysis of conflict and security matters, concluded that Russia has been extensively using GNSS spoofing to divert aerial drones from entering airspace in the vicinity of governmental figures, airports and sea ports2.

During a spoofing attack, modified GPS/GNSS
data is sent into the target receiver, fooling it
into showing a wrong location.
Highly secure anti-spoofing protection with OSNMA
OSNMA secures Galileo signals against spoofing by enabling authentication of navigation data, which carries information about satellite location.
Navigation data security is important because any modification of this information would result in erroneous positioning calculation.
OSNMA makes use of a hybrid Symmetric/Asymmetric cryptography technique. A secret key on the satellite is used to generate a digital signature. Then, both signature and key are appended to the navigation data and transmitted to the receiver.
OSNMA is designed to be backwards compatible — positioning without OSNMA will still work.
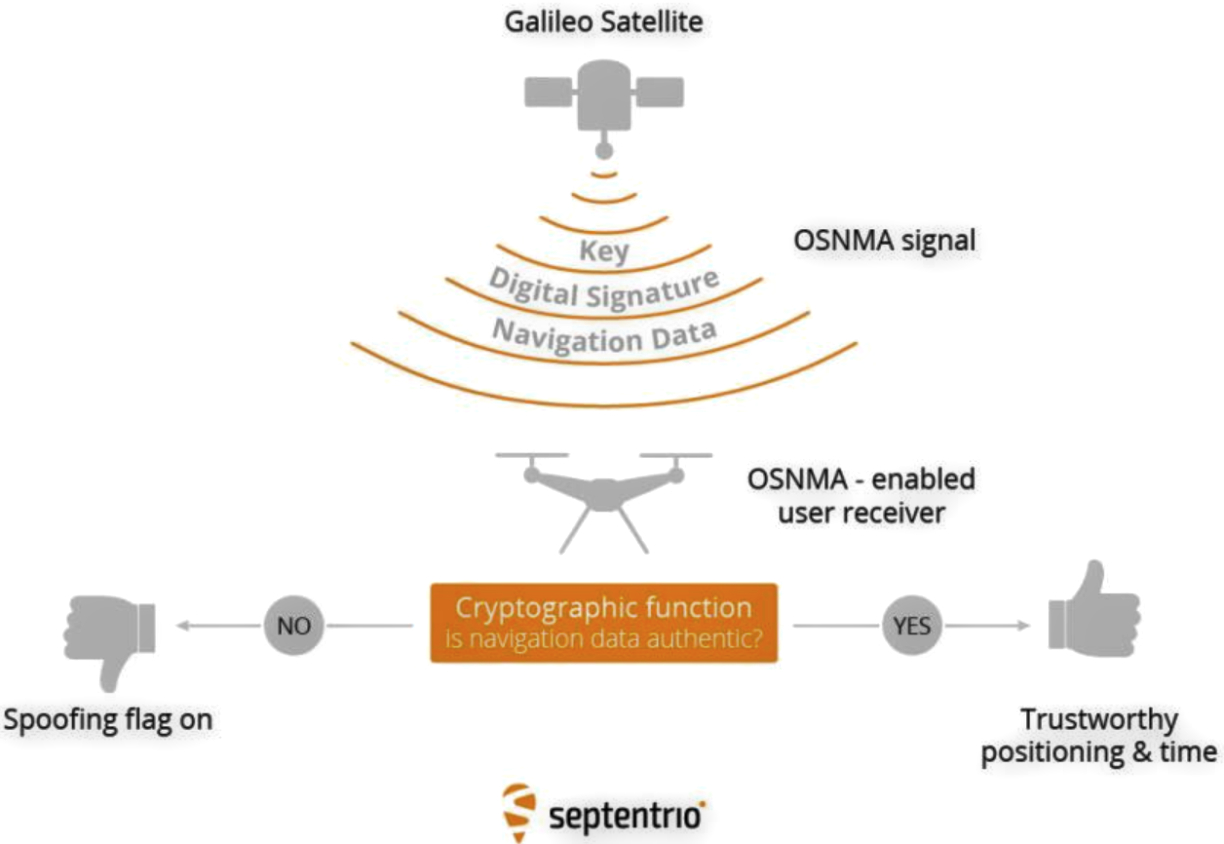
A cryptographic algorithm inside an OSNMA-enabled GNSS receiver authenticates Galileo OSNMA signals.
Authentication with OSNMA-enabled receivers
A sophisticated algorithm within the OSNMA-enabled receiver uses a public key to check the authenticity of the transmitted key. It then uses the transmitted key and the digital signature to check the authenticity of the navigation data. If a satellite signal is flagged as spoofed, it is excluded from the positioning calculation.

OSNMA is one piece of the puzzle comprising a sophisticated interference defense system, such as AIM+ (see image below). For example, AIM+ can also detect spoofing by searching for signal anomalies, such as unusually high power. It also works together with RAIM+ integrity algorithm to ensure range (distance to satellite) validity by comparing ranging data from various satellites.
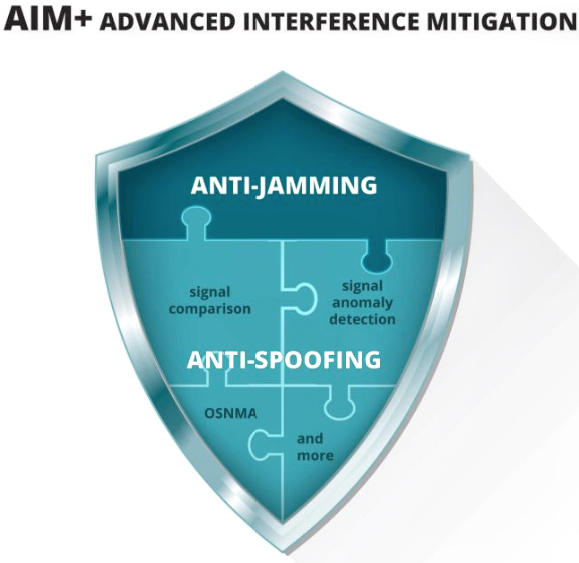
OSNMA is one piece of the puzzle
comprising a sophisticated interference
defense system: AIM+ (Advanced
Interference Mitigation) protecting the
GNSS receiver against jamming and spoofing.
AIM+ won’t even be fooled by an advanced GNSS signal generator, i.e., Spirent GSS9000. Even with realistic power levels and valid navigation data, AIM+ still identifies the simulated signal as “not authentic.” Other advanced, anti-spoofing techniques, such as using a dual-polarized antenna, are currently being developed — read more about this method at this direct infolink.
Future-proof receivers for today and tomorrow
OSNMA is already being implemented to secure synchronization of telecom networks in the GSA-led ROOT project, with Septentrio as a key partner. In the framework of this project, the mosaic-T GNSS module, equipped with AIM+ technology, provides resilient and accurate timing solution to mission critical infrastructure. Various global players, such as Airbus, are the first to try OSNMA authentication of live Galileo signals with specialized Septentrio GNSS receivers. The American GPS system is also developing their own authentication mechanism called Chimera.
Future-proof GNSS receivers are designed in such a way that allows users to take advantage of OSNMA, Chimera and other GNSS value-added services as soon as they become publicly available. Integrating future-proof receivers in high-accuracy solutions allows companies to be the first to market with products or services offering the latest in PNT resilience.

For additional information on spoofing, access “What is spoofing and how to ensure GNSS security.”
1Global Navigation Satellite System including the American GPS, European Galileo, Russian GLONASS, Chinese BeiDou, Japan’s QZSS and India’s NavIC. These satellite constellations broadcast positioning information to receivers which use it to calculate their absolute position.
2Spoofing incidents are regularly reported in the news, read findings about recent spoofing attacks from C4ADS.
www.septentrio.com

