In order to achieve and maintain warfighting overmatch, coordinate deployed forces, and enable new capabilities, the US Army, Air Force and Navy are actively looking to new programs, such as Joint All Domain Command and Control (JADC2) to ensure warfighters have maximum situational awareness.

While the Department of Defense (DoD) intends to rely more heavily on information resources, tactical and expeditionary networking and command post programs widely acknowledge the critical need to improve mobility. This necessitates the implementation of higher-capacity secure wireless, (including for classified networks) available farther out at the edge of the network and across multiple data transport types — to essentially untether communications.
The National Security Agency’s (NSA) Commercial Solutions for Classified (CSfC) program approves organizations to transmit classified information (including Top Secret), via two layers of commercial encryption solutions. By using two sets of encryption technologies (from two different vendors or platforms), one tunneled inside the other, secret information can be transmitted over untrusted wired and wireless networks such as WiFi, LTE, 5G and SATCOM, including public, government, and partner networks.
The CSfC program enables a variety of use cases, but most important is the ability to use commercial wireless mobile devices for classified communications — as well as the ability to use commercial encryption devices for site-to-site transmission of classified information – without the use of Type 1 cryptographic equipment. In the past, the only means available to transmit classified information was via these expensive, controlled, military-grade encryption devices.
For example, with an email server in a classified network, when an email needs to be transmitted over SATCOM, if the email is sent through a VPN encryptor first, the data is encrypted once. Next, after sending that singly encrypted email through a second VPN encryptor — so that it’s encrypted twice — the email can now be safely sent over wireless infrastructure. When the email reaches its destination, it must be decrypted twice. For mobile devices, this can be done using two software-based VPN clients. For remote installations, two gateways can be used, after which, the email can be read on a mobile device using a standard email program.
Figure 1 illustrates how classified information can be transmitted over untrusted wireless networks such as WiFi, LTE, 5G and SATCOM, including public, government, and partner networks.
The ability that CSfC provides to use commercial encryption methods for classified communications has the potential to enable a vast array of use cases. In the same way that consumers have been able to use mobile devices for literally millions of applications, DoD and Federal organizations are just now scratching the surface for how mobile devices can be used in defense and secure use cases. This promises to be especially helpful for supporting network mobility at the tactical edge of the battlefield.
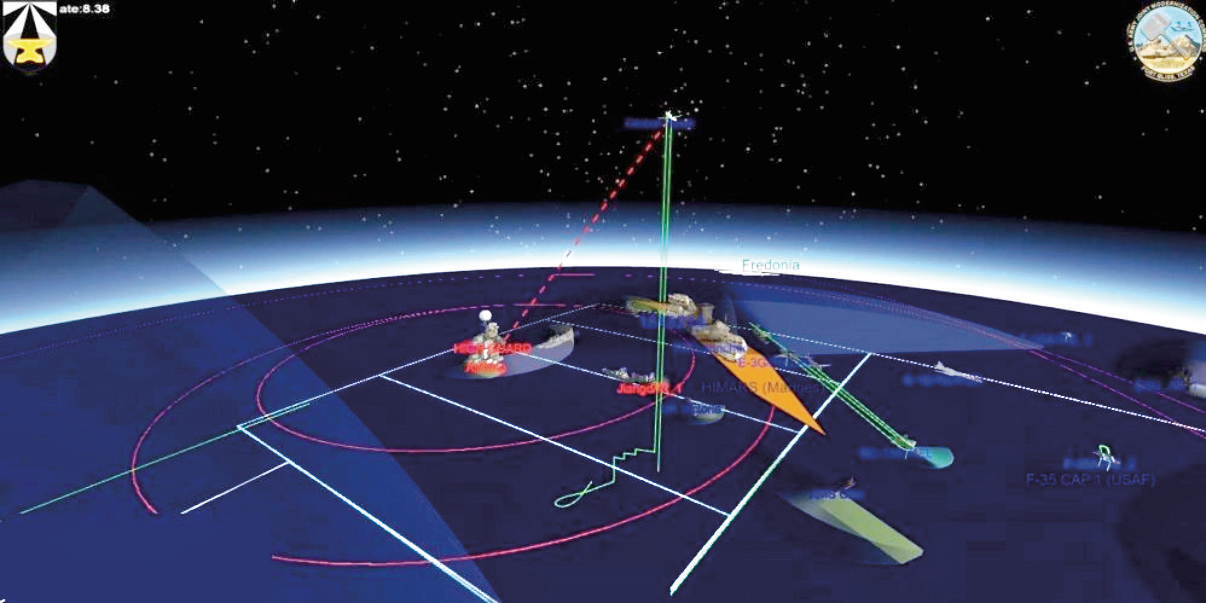
The Joint All-Domain Command & Control (JADC2) is the initiative
to replace the current domain and control systems with one that connects the existing sensors and shooters and distribute the available data to all domains (sea, air, land, cyber, and space) and forces that are part of the U.S. military. Graphic is courtesy of Missile Defence Advocacy Alliance (MDAA) — info@missiledefenseadvocacy.org
Wireless Enables Mobility
Without wireless capability, setting up a network in a brigade command post typically takes hours and requires 17,000 feet CAT 5 cable, which weigh a total of 255 pounds. The cables have to be cut, laid out, configured and plugged in, taking hours for a battalion or brigade command post.
By going wireless, network set up and tear down time is instead reduced to minutes, enabling much greater flexibility so the unit can get up and go as needed.
The US Army PM TN Secure Wireless program has had great success rolling out CSfC for WiFi enabled command posts to reduce setup time and reduce the duration during which they have no situational awareness — and ultimately, to improve command post mobility.
Reducing the time it takes to set up and tear down a command post opens up new options for mobility, whereas in the past, commanders had little choice but to defend a static position.
While improving the setup and tear down time for tent-based command posts is an important improvement for US Army, the vision for next generation command posts includes moving the network infrastructure onto sets of vehicles that can be driven to a location, turn on wireless, and establish full communications between vehicles and in local secure WiFi bubbles. Pilots for these approaches are underway now, using readily available technologies already provenin tent-based command posts, and adapted for vehicle mounted use cases.
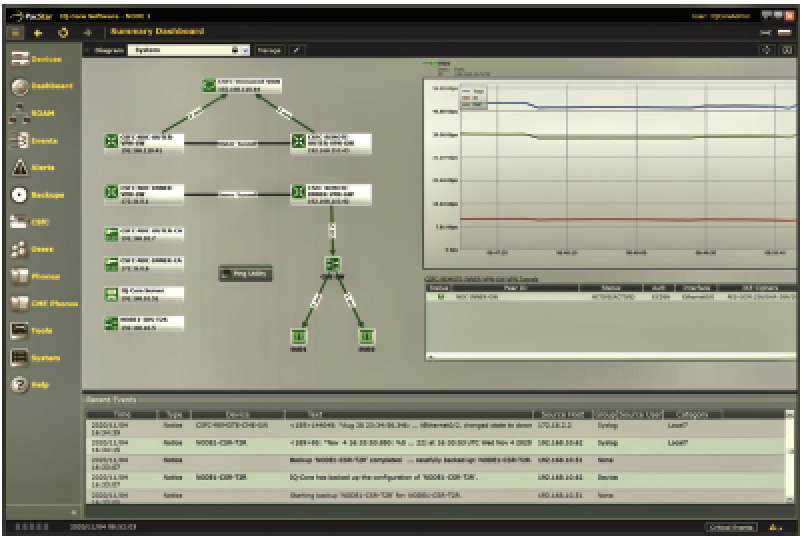 Figure 1.
Figure 1.
Similar to what’s happening in tactical programs, DoD enterprise organizations are increasingly looking to create enterprise gateways to support remote workers on mobile devices or at remote sites, for DoD and civilian applications, as well as for partner missions.
CSfC offers benefits for any organization that has classified or mission-critical secure communications requirements for remote sites, remote workers or partner organizations.
Though the concept of dual layered encryption is fairly straightforward, full CSfC implementations must include a breadth of technologies or components, including public key infrastructure (PKI), encryption gateways and clients, authentication systems, cybersecurity technologies, and secure network infrastructure. These components must first have their cryptographic implementations validated to FIPS 140 standards through the NIST Crypto Module Validation Program.
Next, the CSfC components must be Common Criteria validated against one or more protection profiles, such as VPN Gateway, TLS protected application, or WiFi access system. Additionally, certified PKI is required for certificate (or key) management.
These validations are typically sponsored by commercial vendors, and conducted by recognized testing labs. Once the validation step is complete, the products, such as a VPN Gateways, are placed on NSA’s CSfC Components List, making them eligible for use, off-the-shelf, in CSfC Solutions. It should be noted that while components on the list are eligible for use nothing in the component validation processes establishes interoperability or the ability of a product to meet NSA system-level requirement.
Integrators must select from the products on the components list to create solutions that conform to one of the NSA Capability Packages such as, for mobile device access, WiFi access or site-to-site transmission Once a solution has been assembled, they must validate that the solution functions as intended and meets Capability Package threshold requirement before the system is submitted for registration (approval) by NSA’s CSfC PMO.
Curtiss-Wright’s PacStar business has extensive expertise in CSfC, having designed, built and delivered numerous deployed CSfC solutions to protect critical data-in-motion over the last six years. The company does this with three categories of products:
► Small form factor, rugged hardware — popular in many US and partner tactical network programs.
► IQ-Core Software, a single pane of glass to manage tactical networking equipment. This is widely deployed, particularly across large numbers of programs in US Army.
► PacStar Integrated Solutions — combining our hardware, IQCore Software, and vast arrays of 3rd party virtualized network functions, cybersecurity tools and application software — into turnkey solutions.
In addition to PacStar’s CSfC solutions, Curtiss-Wright’s Data Solutions business offers high-density storage solutions with CSfC approval for use in classified data-at-rest encryption. Curtiss-Wright’s Parvus product line offers rugged CSfC-approved modules for data-in-transit — thus, the combination of products across the Curtiss-Wright Defense Solutions businesses enable CSfC use cases across nearly every type of application.
The combination of CSfC mobility and wireless solutions provides enormous potential to enable command post mobility, soldier-dismounted situational awareness, vehicle-to-vehicle communications and much more.
In order to satisfy CSfC and DoD guidelines for classified networking, it’s important for defense programs, systems integrators, and technology developers to understand the extensive set of complex requirements and processes involved in realizing an NSA approved two-layer encryption solution. Fortunately, the CSfC program has developed extensive guidance materials on the NSA web site, and the industry hosts annual CSfC-focused conferences for education and collaboration.
In addition, NSA has developed a vibrant eco-system of trusted integrators and technology developers, such as Curtiss-Wright, that can guide integration efforts and make CSfC implementations successful.
www.curtisswright.com/home/default.aspx

Charlie Kawasaki, CISSP, joined PacStar in early 2005. He is the company Chief Technical Officer and leads multiple innovation initiatives including development of cutting-edge tactical computing systems. Charlie also serves as a Commercial Solutions for Classified (CSfC) subject matter expert.
Charlie is part of the PacStar team that won tactical networking equipment and software awards for numerous DoD tactical programs including the US Army T2C2, US Army SFAB, US Army ESB-E, PM TN Secure Wireless Gateway, PEOC3T TCNO, and US Marine Corps NOTM vehicle-mount and deployable communications programs.
He has more than 40 years’ experience in network engineering, machine learning/ AI, systems integration, software engineering, and cybersecurity. Prior to joining PacStar, Charlie provided his expertise to early stage technology companies, where he created dozens of software and networking-based products. Charlie served as CEO of RuleSpace, Inc., which created AI-based technology for Internet parental controls used by companies such as AOL, Yahoo, SBC, BellSouth, and Microsoft.


