The U.S. Department of Defense (DoD) is increasingly concerned about security and the availability of tactical networks and tactical communications for traditional command and control (C&C), surveillance and reconnaissance activities, while simultaneously increasing the reliance on networking for new capabilities such as coordination of joint/coalition warfighting, electronic and cyber warfare, and fielding unmanned and robotic systems. Recent advances in mobile devices also increase the DoD’s reliance on secure wireless networking.

An example of the small form factor server running PKI technology as compared to a standard size server.
When warfighters operate in forward positions or contested territory, their communications networks are exposed more directly to adversaries as a simple result of proximity. Furthermore, lack of terrestrial infrastructure and the need for mobility increase their reliance on wireless communications, exposing tactical communications and networks to interception and wireless attack. To ensure the security of these communications, encryption is a first line of defense.
To meet the increasing security needs of tactical networks and to enable the proliferation of new devices and capabilities using secure tactical networking, the DoD is increasingly looking to Public Key Infrastructure (PKI) as a primary means to manage identity/authentication
and encryption.
PKI is making its way into tactical networks and onto devices used in tactical settings to enable:
a. Access to enterprise applications — frequently using web servers with PKI enabled HTTPS security.
b. Tactically deployed applications, also using web servers protected with HTTPS.
c. Encryption of long-distance wireless communications links enabling communications between tactical units and bases or HQ — such as with satellite communications (SATCOM).
d. Encryption for wireless devices such as smart phones, tablets and laptops — in command posts or for dismounted soldiers.
e. Encryption for communications between coalition forces.
PKI-enabled security is replacing older security technologies based on passwords, “pre-shared keys” (PSK), and government-developed classified encryptors. PKI is today’s technology of choice because of its wide support in enterprise and internet-based companies, abundance of mature commercial technologies and strong security properties.
However, PKI is poorly understood and has complexities that have slowed adoption in tactical networks — challenges that are now being addressed, in part, by new Commercial-Off-The-Shelf (COTS) technologies that aim to ease deployment. This will pave the way to make the benefits of PKI-based security available to tactical networks with a minimum of cost and difficulty.
What is PKI?
At the highest level, PKI is a set of software and hardware technologies designed to manage the creation, storage, transmission and authentication of digital certificates and their associated encryption keys. A real world analogy to a digital certificate is a driver’s license.
In the digital realm, a digital certificate serves as a way for a person or device to prove who they are, because a part of the PKI known as a Certificate Authority (CA) has issued and “signed” the certificate vouching for the person.
PKI-enabled systems provide strong authentication and encryption of data by using cryptographic functions. Unlike traditional identity processes, where users are identified by passwords, a PKI issues a certificate via known, trusted channels and binds the certificate to a cryptographic key pair. The key pair consists of a widely shared public key, and the holder of the certificate maintains a private key that is unknown to anyone else. A cryptographic function ties these two keys together so that actions performed by one, can be verified or decrypted by the other.
Why is PKI better?
PKI-based networks have significantly stronger security than networks that rely on passwords (and all of their known weaknesses) and has significantly better manageability properties than other encryption schemes such as pre-shared keys. Specifically:
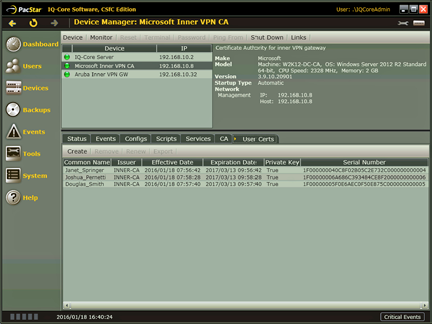
Screen capture of the integrated user interface for managing tactical PKI infrastructure including Certificate Authorities and VPN gateways.
• PKI-based systems enable authentication and encryption to occur without the need to ever share highly confidential private keys.
• The keys in PKI-based systems can be used for one-way encryption functions where only the designated owner of the key can decrypt data. This prevents Man-in-the-Middle attacks without knowledge of the key pair.
• Certificates used in PKI-based systems can be easily revoked (such as in the event of a lost or stolen device).
• As opposed to PSK-based systems, PKI-based systems do not require unique sets of keys for all combinations of devices that must communicate with one another.
Instead, a server only stores its own key pair and does not have to store all of the clients’ keys. This dramatically reduces the workload required to manage sets of keys, and allows the number of network devices and users to scale to large numbers.
By leveraging a PKI, VPN environments can vastly improve their security posture. Cryptographic keys can’t be socially engineered or easily stolen, so by requiring a certificate to authenticate to a VPN, organizations can have a much higher level of assurance of who or what is connecting to the network.
For applications such as HTTPS protected web sites or web applications, Transport Layer Security (TLS) uses certificates to identify hosts providing TLS services and to bootstrap the encryption process for clients and servers. TLS can also be used to support client-side authentication where clients must present a certificate to authenticate to a website rather than using password based authentication. This mutual authentication ensures both parties are able to positively identify the other.
Challenges with Tactical PKI
Similar to most advanced technologies, to gain the benefits of PKI in tactical networks, DoD organizations must implement technology, processes, procedures and training. While PKI provides a compelling set of scalability, manageability and security improvements over alternative key management schemes, rollout and deployment has side effects that require careful planning and consideration.
Some of these challenges include requirements to:
• Acquire, configure, integrate, secure and manage multiple Certificate Authorities (with matching hardware security modules)
• Enable network access to CAs and the systems managing lists of revoked certificates
• Provisioning of devices including infrastructure and end-user devices, to use certificates and key pairs
• Developing certificate handling procedures and policies, including processes to monitor and renew expiring certificates
• Training security and system administrators to configure, monitor, and troubleshoot PKI-based systems
Without careful attention to all of the items above, tactical communications systems may fail to establish encrypted communications or may expose security vulnerabilities.
Common failures include:
• Generation of certificates that are incompatible with PKI-enabled devices/infrastructure.
• Device certificates expiring (each certificate must include an expiration date) during critical operations or at a location where a Warfighter does not have access to systems enabling renewal.
• Mismatches between the date/time settings of devices, causing communication failures.
• Inability of devices to communicate with systems providing certificate revocation status.
• Loss or theft of certificates.
Tactical PKI Solutions to Consider
To successfully deploy tactical PKI, organizations should consider new developments in commercial-off-the-shelf technologies that can ease the complication and expense of deploying tactical PKI, while maximizing the security benefits. These technologies include:
• Small form factor tactical PKI appliances
These appliances can host Certificate Authorities, Certificate Revocation List and PKI-enabled authentication systems. These solutions can minimize the size, weight and power impacts of the added security components required to forward deploy PKI, ensuring certificate generation and renewal can be accomplished in the field.
Small form factor tactical network appliances
PKI-enabled network appliances include VPN gateways, wireless mobility controllers, and web servers. These solutions can minimize the size, weight and power impacts of the added security components required to deploy PKI-enabled encryption.
• PKI-optimized network and device management software
This type of software can simplify the management of certificates, streamline the device provisioning and certificate renewal process, and configure network devices to use PKI correctly. These solutions can reduce the training burden and eliminate configuration errors common with PKI administration tasks — enabling lightly trained communications specialists to use PKI with confidence.
Maximizing PKI’s Benefits
PKI is increasingly in use by tactical networks and devices because of its maturity, interoperability, security and scalability.
To maximize the benefit from PKI’s advantages, tactical network programs should consider using new COTS technologies to reduce the SWaP impact of fielding PKI systems and to reduce the added complexity and training associated with using the systems. Doing so will enable tactical networks to modernize their security posture, enable new secure communications capabilities and assist our defense organizations in meeting their mission.
pacstar.com/

Charlie Kawasaki is CTO for PacStar, a developer of secure tactical communications solutions. He has 35 years’ experience in the software, networking and cybersecurity industry. He is a subject matter expert in the NSA Commercial Solutions for Classified program that makes extensive use of PKI for transmission of classified information.

Mark B. Cooper, President and Founder of PKI Solutions, Inc., has 27 years’ experience in the IT industry and is an internationally recognized expert in PKI, including 10 years’ experience at Microsoft where he advised Enterprises in their Microsoft-based PKI design and implementation.


